利用二層端口安全防止兩個三層交換機長距離光纖線路被亂接測試
一.概述:
在論壇上看到有人想問通過什么方式來防止長距離的光纖線路被竊聽,或連到其它非法交換機上,如是相同通過端口安全來實現防止亂接,于是登錄機架進行測試,將測試結果記錄下來。
論壇提問的鏈接:http://bbs.51cto.com/thread-1080361-1.html
----光纖線路,如果中間沒有被惡意接入其他設備,應該很難竊聽,因此覺得防竊聽可以從防亂接方向入手。
二.基本思路:
A.假定交換機為三層交換機
B.如果兩個交換機用三層口相連,并綁定對端IP所對應的mac,雖然可以防止接入三層設備,但是無法防止中間串接二層設備進行竊聽。
C.通過主機之間的ipsec來加密流量,除非接線兩端為路由器,否則兩端連接交換機的主機太多的話,每臺主機去配置IPsec不大可行。
-----高端的交換機沒有玩過,一般普通的三層交換機貌似無法配置ipsec ***
D.數據加密雖然是防竊聽的最好方式,但是目前這種情況,貌似加密不容易實現
E.通過二層的安全來防止亂接:
---交換機相連的口采用access口,并且兩端都配置VLAN的svi
---每個交換機保證用于互聯的vlan只有一個互聯接口
---三層交換機要開啟路由轉發,兩個三層交換機互指路由(靜態或默認),來實現交換機兩邊的PC互訪
---配置互聯端口的端口安全,只允許學習到2個mac,這樣只有中間線路沒有其他二層設備,當接入其他二層設備時,端口就會down,防止被監聽
---本實驗只是驗證可行性,實際工作如果可能的話,還是建議用路由器互聯,并配置ipsec。
三.測試拓撲:
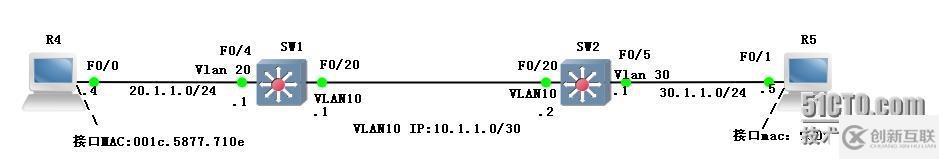
四.基本配置:
A.R4:interface FastEthernet0/0
ip address 20.1.1.4 255.255.255.0
ip address 20.1.1.4 255.255.255.0
no shut
no ip routing
ip default-gateway 20.1.1.1
B.SW1:
ip routing
interface FastEthernet0/4
switchport access vlan 20
switchport mode access
switchport access vlan 20
switchport mode access
interface FastEthernet0/20
switchport access vlan 10
switchport mode access
switchport port-security maximum 2
switchport port-security
switchport port-security mac-address sticky
switchport access vlan 10
switchport mode access
switchport port-security maximum 2
switchport port-security
switchport port-security mac-address sticky
interface Vlan10
ip address 10.1.1.1 255.255.255.252
interface Vlan20
ip address 20.1.1.1 255.255.255.0
ip route 0.0.0.0 0.0.0.0 10.1.1.2
ip address 10.1.1.1 255.255.255.252
interface Vlan20
ip address 20.1.1.1 255.255.255.0
ip route 0.0.0.0 0.0.0.0 10.1.1.2
C.SW2:
ip routing
interface FastEthernet0/5
switchport access vlan 30
switchport mode access
switchport access vlan 30
switchport mode access
interface FastEthernet0/20
switchport access vlan 10
switchport mode access
switchport port-security maximum 2
switchport port-security
switchport port-security mac-address sticky
switchport access vlan 10
switchport mode access
switchport port-security maximum 2
switchport port-security
switchport port-security mac-address sticky
interface Vlan30
ip address 30.1.1.1 255.255.255.0
interface Vlan100
ip address 10.1.1.2 255.255.255.252
ip route 0.0.0.0 0.0.0.0 10.1.1.1
interface Vlan100
ip address 10.1.1.2 255.255.255.252
ip route 0.0.0.0 0.0.0.0 10.1.1.1
D.R5:
interface FastEthernet0/1
ip address 30.1.1.5 255.255.255.0
ip address 30.1.1.5 255.255.255.0
no shut
no ip routing
ip default-gateway 30.1.1.1
五.驗證:
R4#ping 30.1.1.5
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 30.1.1.5, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/4 ms
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 20.1.1.4, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/2/4 ms
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 30.1.1.5, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/4 ms
R4#
R5#ping 20.1.1.4Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 20.1.1.4, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/2/4 ms
R5#
sw1#show running-config interface f0/20
Building configuration...
Current configuration : 336 bytes
!
interface FastEthernet0/20
switchport access vlan 10
switchport mode access
switchport port-security maximum 2
switchport port-security
switchport port-security mac-address sticky
switchport port-security mac-address sticky 0014.a80a.f716 vlan access
switchport port-security mac-address sticky 0014.a80a.f741 vlan access
end
Building configuration...
Current configuration : 336 bytes
!
interface FastEthernet0/20
switchport access vlan 10
switchport mode access
switchport port-security maximum 2
switchport port-security
switchport port-security mac-address sticky
switchport port-security mac-address sticky 0014.a80a.f716 vlan access
switchport port-security mac-address sticky 0014.a80a.f741 vlan access
end
sw2#show int f0/20 | in Hardware
Hardware is Fast Ethernet, address is 0014.a80a.f716 (bia 0014.a80a.f716)
Hardware is Fast Ethernet, address is 0014.a80a.f716 (bia 0014.a80a.f716)
sw2#show int vlan 10 | in Hardware
Hardware is EtherSVI, address is 0014.a80a.f741 (bia 0014.a80a.f741)
Hardware is EtherSVI, address is 0014.a80a.f741 (bia 0014.a80a.f741)
sw1#show mac address-table | in 0/20
10 0014.a80a.f716 STATIC Fa0/20
10 0014.a80a.f741 STATIC Fa0/20
sw1#
10 0014.a80a.f716 STATIC Fa0/20
10 0014.a80a.f741 STATIC Fa0/20
sw1#
sw2#show running-config int f0/20
Building configuration...
Current configuration : 312 bytes
!
interface FastEthernet0/20
switchport access vlan 10
switchport mode access
switchport port-security maximum 2
switchport port-security
switchport port-security mac-address sticky
switchport port-security mac-address sticky 001a.a164.b216
switchport port-security mac-address sticky 001a.a164.b241
end
Building configuration...
Current configuration : 312 bytes
!
interface FastEthernet0/20
switchport access vlan 10
switchport mode access
switchport port-security maximum 2
switchport port-security
switchport port-security mac-address sticky
switchport port-security mac-address sticky 001a.a164.b216
switchport port-security mac-address sticky 001a.a164.b241
end
sw1#show int f0/20 | in Hardware
Hardware is Fast Ethernet, address is 001a.a164.b216 (bia 001a.a164.b216)
sw1#show int vlan 10 | in Hardware
Hardware is EtherSVI, address is 001a.a164.b241 (bia 001a.a164.b241)
Hardware is Fast Ethernet, address is 001a.a164.b216 (bia 001a.a164.b216)
sw1#show int vlan 10 | in Hardware
Hardware is EtherSVI, address is 001a.a164.b241 (bia 001a.a164.b241)
sw2#show mac address-table | in 0/20
10 001a.a164.b216 STATIC Fa0/20
10 001a.a164.b241 STATIC Fa0/20
---因為機架無法默認中間加入其它二層設備,但是可以通過往互聯接口所在vlan添加其他接口來測試,因為接口收到其他mac地址的包,接口會down。10 001a.a164.b216 STATIC Fa0/20
10 001a.a164.b241 STATIC Fa0/20
網站題目:利用二層端口安全防止兩個三層交換機長距離光纖線路被亂接測試
轉載來源:http://vcdvsql.cn/article26/gjgecg.html
成都網站建設公司_創新互聯,為您提供商城網站、建站公司、外貿網站建設、網站制作、網站改版、虛擬主機
聲明:本網站發布的內容(圖片、視頻和文字)以用戶投稿、用戶轉載內容為主,如果涉及侵權請盡快告知,我們將會在第一時間刪除。文章觀點不代表本網站立場,如需處理請聯系客服。電話:028-86922220;郵箱:631063699@qq.com。內容未經允許不得轉載,或轉載時需注明來源: 創新互聯

- 深圳服務器托管費用,深圳托管一臺服務器多少錢 2021-03-20
- 網站服務器托管價格有哪些影響因素? 2022-10-02
- 企業服務器托管有什么技巧?企業服務器托管該注意哪些問題? 2022-10-02
- 服務器托管租用給企業帶來的好處 2016-11-02
- 服務器托管與租用報價波動原因是什么呢? 2022-10-08
- 服務器中毒處理 2022-05-25
- 服務器托管使用固態硬盤好嗎 2022-10-08
- 服務器托管租用什么意思? 2022-10-06
- 服務器托管商一定要避免的9種機房現狀 2022-10-07
- 避免服務器托管浪費成本,這些問題要知道 2022-10-12
- IDC服務器托管是什么?為什么要托管? 2022-10-04
- 為什么要服務器托管?什么是IDC服務器托管? 2022-10-05